 More information about CSE's employee strength
and authorized establishment.
More information about CSE's employee strength
and authorized establishment.
What is the Communications Security
Establishment?
Overview and Brief History
Policy, Operational and Administrative Control
Mandate
CSE/SRS Facilities
New Targets?
Recent Steps Toward Oversight
Strictly speaking, CSE is only part of Canada's SIGINT effort. A civilian agency of the Department of National Defence, CSE processes SIGINT, produces analyses, and disseminates reports to Canadian and allied consumer agencies. The actual collection of the SIGINT, however, is conducted by the Canadian Forces Supplementary Radio System (SRS), a component of the Canadian Armed Forces that operates under the direction of CSE.
CSE and the SRS in turn work in close co-operation with the giant American and British SIGINT agencies, the National Security Agency (NSA) and Government Communications Headquarters (GCHQ), Australia's Defence Signals Directorate (DSD), New Zealand's Government Communications Security Bureau (GCSB), and a number of other SIGINT agencies in a global intelligence alliance known informally as the UKUSA community. CSE maintains permanent liaison officers at NSA HQ at Fort Meade, Maryland (CANSLO/W) and GCHQ in Cheltenham, UK (CANSLO/L). There are also NSA and GCHQ liaison officers at CSE HQ (SUSLO/O and BRLO, respectively). For more information about NSA, see the official NSA homepage or the much more informative Federation of American Scientists NSA homepage. For more information about GCHQ, see the IntelWeb GCHQ page.
In 1947, CBNRC took on the additional responsibility of serving as the Canadian government's communications-electronic security (COMSEC) agency. Prior to 1947, the government's encryption systems and keys had been provided by the United Kingdom. ``This arrangement,'' the History of CBNRC noted dryly, ``did not guarantee the privacy of Canadian government classified communications.''[3] CSE continues to bear both SIGINT and COMSEC responsibilities today (the latter responsibility is now listed as the somewhat broader category Information Technology Security (INFOSEC)). For more about CSE's INFOSEC mandate and current INFOSEC activities, see the official CSE homepage.
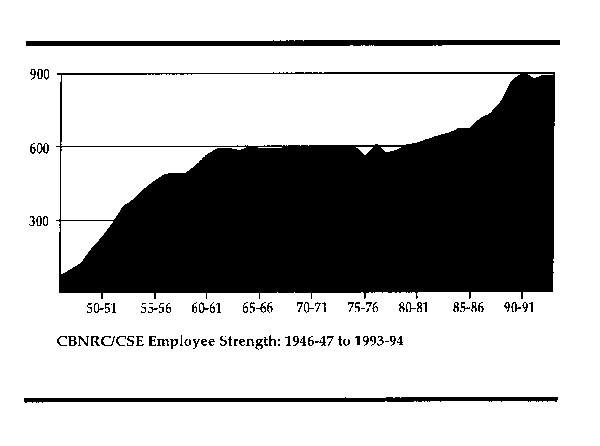
On 1 April 1975, CBNRC was transferred from the National Research Council to the Department of National Defence and its name changed to the Communications Security Establishment. At the time of its transfer, CBNRC/CSE had about 590 personnel. A major buildup during the period 1981-1990 left CSE at its current strength of about 900.[4]
The following graph depicts CSE's employee strength from 1946-47 to 1993-94.
 More information about CSE's employee strength
and authorized establishment.
More information about CSE's employee strength
and authorized establishment.
More about CSE's history.
The current Chief of CSE is A. Stewart Woolner. Under the Chief are five Directorates (Policy and Plans; SIGINT Production; Technology; INFOSEC; and Administration), each headed by a Director-General. Each Directorate, in turn, contains a number of Groups, each headed by a Director. An approximation of CSE's overall organization is depicted in this organization chart.
Information about CSE's Badge.
 A unified collection
organization, the Supplementary Radio System (SRS), was created in 1966 as
part of the unification of the Canadian Armed Forces. The SRS remains
responsible for the ``operation and maintenance of facilities dedicated to
the signals intelligence collection role and high frequency radio
direction-finding services.''[5]
A unified collection
organization, the Supplementary Radio System (SRS), was created in 1966 as
part of the unification of the Canadian Armed Forces. The SRS remains
responsible for the ``operation and maintenance of facilities dedicated to
the signals intelligence collection role and high frequency radio
direction-finding services.''[5]
As of the beginning of 1995, the strength of the SRS, counting civilian support staff at the SIGINT stations, was probably about 1250-1300; perhaps 900 of these were members of the Communicator Research (291) trade, i.e., the actual intercept operators.
In practice, policy and operational control is exercised by the Deputy Clerk (Security and Intelligence, and Counsel) and the Intelligence Advisory Committee, both of the Privy Council Office, working under the direction of the Interdepartmental Committee on Security and Intelligence (ICSI) and, ultimately, the Cabinet Committee on Security and Intelligence (CCSI). ``The ICSI maintains general policy control over all aspects of the collection, processing and dissemination of SIGINT and exercises this control through the Intelligence Advisory Committee (IAC) for national SIGINT, and the Canadian Forces for tactical COMINT and ELINT.''[7] The Chief of CSE is an associate member of the ICSI.[8]
Among its other duties, the IAC ``co-ordinates the Canadian SIGINT program with other national intelligence activities and formulates guidance, requirements and priorities for the provision of SIGINT product.''[9] (Some user requirements are also provided to CSE bilaterally by SIGINT customer departments.)
Administrative control is exercised by the Minister and Deputy Minister of the Department of National Defence. ``The Minister approves CSE's major capital expenditures, its annual Multi-Year Operation Plan, and (with CCSI) major CSE initiatives with significant policy or legal implications.''[10]
The Minister of National Defence is the member of Cabinet accountable to Parliament for CSE.[11] It is the responsibility of the Deputy Clerk (Security and Intelligence, and Counsel), ``in co-operation with the deputy minister of National Defence, to ensure the Minister of National Defence [is] knowledgeable about matters of CSE, and able to respond to any questions that would be put on that subject.''[12] In practice, however, it is likely that few ministers of National Defence ever obtain a detailed knowledge of the nature and activities of CSE. Former Minister of National Defence Jean-Jacques Blais has stated, for example, that ``my knowledge of the Communications Security Establishment was very superficial indeed when I was minister of defence.''[13]
Control over INFOSEC activities is organized similarly, except that it is exercised through the Security Advisory Committee of the PCO instead of the Intelligence Advisory Committee.
The Canadian public has been told on a number of occasions that CSE's formal mandate restricts it to the collection of ``foreign intelligence''.[15] The government's definition of SIGINT, quoted at the beginning of this chapter, would appear to confirm this assurance.
It is almost certainly significant, however, that the government definition of ``foreign'' communications has never been made public; it was deleted in its entirety from the released version of IAC SIGINT Memorandum No. 1. Depending on the precise definition that the government uses, such communications might include:
It would appear, therefore, that CSE's ``foreign intelligence'' mandate does permit it to intercept many types of communications that do involve Canadian participants. In fact, the Department of National Defence has admitted that CSE occasionally intercepts communications that involve or contain information about Canadians: ``CSE targets only foreign communications, which, on rare occasions, contain personal information about Canadian citizens and landed immigrants.''[17] In addition, the government has confirmed that CSE maintains a data bank, DND/P-PU-040, ``Security and Intelligence Information Files,'' that contains ``information concerning [Canadians] identified as potential risks to national security.''[18] Nevertheless, the issue of how often and how systematically CSE can and does intercept the communications of Canadians remains unresolved. More on CSE and Canadian communications.
For obvious reasons, the identity of these new targets has not been revealed. It is almost certain, however, that they are located among the growing volume of civilian traffic carried by satellite. The communications satellites that serve Latin America are more likely to be the targets of this expansion than Canadian satellites are, but any step towards the more systematic monitoring of civilian communications should be of concern. Who will be targeted next?
The Chretien government initially also maintained that CSE did not require independent oversight. To its credit, however, on 21 March 1995 it permitted the passage of a motion by MP Derek Lee calling on the government to ``establish an independent external mechanism to review the operations of the Communications Security Establishment, CSE, similar to the role played by the Security Intelligence Review Committee for the Canadian Security Intelligence Service, and table a report annually in the House.''[22] The following day, Defence Minister David Collenette announced that the government would indeed establish such a mechanism. He did not, however, provide any details of the government's plans, stating only that, ``in principle, the government supports an oversight mechanism for the CSE.''[23]
The above analysis suggests that a truly effective oversight mechanism would require:
[2] For more information on Canada's wartime SIGINT activities, see John Bryden, Best-Kept Secret: Canadian Secret Intelligence in the Second World War, Lester Publishing, 1993.
[3] History of CBNRC, Chapter 17, p. 2.
[4] Ward Elcock, testimony, Minutes of Proceedings and Evidence of the Sub-Committee on National Security, 15 June 1993, p. 11:9; Statement by Margaret Bloodworth, Deputy Clerk, Security and Intelligence, to Standing Committee on National Defence and Veterans Affairs, 2 May 1995.
[5] Defence 90, Supply and Services, 1991, p. 48.
[6] On Course: National Security for the 1990s, Solicitor General, 1991, p. 54.
[7] History of CBNRC, Chapter 2, Annex G.
[8] Ward Elcock, testimony, Minutes of Proceedings and Evidence of the Special Committee on the Review of the Canadian Security Intelligence Service Act and the Security Offences Act, 24 April 1990, p. 27:9.
[9] History of CBNRC, Chapter 2, Annex G.
[10] On Course, p. 54.
[11] On Course, p. 54.
[12] Blair Seaborn, testimony, Minutes of Proceedings and Evidence of the Special Committee on the Review of the Canadian Security Intelligence Service Act and the Security Offences Act, 20 February 1990, p. 16:9.
[13] Quoted in Peter Moon, ``Spy agency left minister in dark,'' Globe and Mail, 3 June 1991, p. A4. Elsewhere Blais has commented that ``While I had responsibility for the estimates presented to Parliament, that responsibility did not extend to the exercise of ministerial control over the CSE. In practice the control was bureaucratic, in my view short-circuiting the principle of political accountability on which our democracy is founded.'' (Jean Jacques Blais, ``Committee should be expanded to review other agencies,'' Ottawa Citizen, 2 July 1992, p. A11.)
[14] History of CBNRC, Chapter 2, Annex G
[15] See, e.g., Minister of State (External Relations) Jean-Luc Pepin, testimony, Proceedings of the Special Committee of the Senate on the Canadian Security Intelligence Service, 22 September 1983, p. 19.
[16] Robert Kaplan, testimony, Minutes of Proceedings and Evidence of the Standing Committee on Justice and Legal Affairs, 5 April 1984, p. 11:68.
[17] Letter from Commander F.B. Frewer, Director Public Affairs Operations, National Defence, to Peter Moon, 15 April 1991.
[18] Personal Information Index 1988, 1988, p. 47- 3.
[19] In Flux But Not in Crisis, report of the Special Committee on the Review of the Canadian Security Intelligence Service Act and the Security Offences Act, September 1990, pp. 152-3; Annual Report 1988-89, Security Intelligence Review Committee, 1989.
[20] On Course, p. 55.
[21] There is little reason to expect that CSE has been any more reliable in this respect. See, for example, the allegations in the book Spyworld (Mike Frost and Michel Gratton, Spyworld: Inside the Canadian and American Intelligence Establishments, Doubleday Canada, 1994) concerning the interception of Quebec government communications. In 1991, ``former CSE employees and other sources,'' told the Globe and Mail that ``in the past the agency routinely broke Canadian laws in the collection of intelligence involving Canadians.'' (Peter Moon, ``Secrecy shrouds spy agency,'' Globe and Mail, 27 May 1991, pp. A1, A4.) This allegation has not been proven, but a disquieting example of CSE failing to follow appropriate procedures and respect the rights of one of its own employees is on the public record in Muriel Korngold Wexler, Record of Decision (file 166-13-17850), Public Service Staff Relations Board, 12 March 1990. This document includes a detailed description of the mistreatment and eventual unjust firing of CSE cryptanalyst Edwina Slattery during the 1980s. It should be noted that Ms. Slattery considers the Record of Decision's description of the events surrounding her firing to be inaccurate in many respects, notwithstanding the fact that it supported her claim that she had been unjustly fired and recommended that she receive compensation equivalent to two years' pay. Ms. Slattery continues to pursue the case in the Federal Court of Canada.
[22] House of Commons Debates, 21 March 1995, pp. 10815-10820.
[23] Tu Thanh Ha, ``Secretive agency to be more open, Collenette says,'' Globe and Mail, 23 March 1995, p. A5.
|
To be contacted for a confidential consultation please E-mail: jmatk@tscm.com
or send a letter via US Mail to:
or call:
URL: http://www.tscm.com/ |