
Major "Real-World" Bugging Frequencies
The frequencies that follow are all based on hard documentation (catalogs, intelligence reports, technical materials, court documents, and specific device protocols). For the purpose of analysis the Source Reliability Scale should be considered A, and the Data Validity Scale should be rated as 1.
If the TSCM specialist already knows what frequency the RF eavesdropping device is (or may be) operating on, then the detection of the device becomes several orders of magnitude easier. For example a very popular "SpyShop" bug frequency is 398.605 MHz, 300.455 MHz, and 399.030 MHz. By configuring a modern spectrum analyser or receiver and targeting the specific parameters of this device it may be found from hundreds, and often thousands of feet away. There are roughly 3500 popular "bugging" frequencies used by the various Spy Shops devices around the world. It takes less then 5 minutes for a computer controlled radio to check all 3500 channels. Of course the entire RF spectrum still has to be checked in detail (which takes many hours), but knowing what specific frequencies might be used by the opposition gives the TSCM specialist a major advantage.
Remember to check the entire RF spectrum, not just specific frequencies; however, keep in mind that people doing bugging like to stay clustered around certain frequencies (it's one of their trade craft errors that can be exploited to bring about their demise).

Several PI schools, TSCM schools, and spy shops sell equipment (at highly inflated prices) and actively attempt to mislead students that all they have to do is spend a few hundred to a few thousand dollars on equipment to enter the TSCM field. Markup on these bogus products are typically greater than 400%, and what the spy school buys or builds for $100 they sell to their gullible customers for thousands or even tens of thousands of dollars.
For every legitimate TSCM firm there are 500 con artists (cloak and dagger types) who buy "CIA Bug Detectors" for $ 50 and resell them to their corporate clients for $ 8,500 (it's usually just a primitive broadband diode detector system). They remove the original markings and apply a stick-on labels with their name. Often they will even reprint the operators manual with their own logo and name. Some will even go so far as to have the client sign bogus security clearance or confidentiality documents to make the transaction appear even spookier. These spy-shops are trying to modify reality and the laws of physics to help them pad their bank accounts. Beware, Beware, Beware...
The frequency coverage of these special spy-shop bug detectors generally "top-out" at 1 GHz, with adapters and mixers the range they can sometimes be increased to 2-3 GHz. They are very limited value in finding bugs and tend to create a dangerous false sense of security.
|
Therefore, I say: Know your enemy and know yourself; in a hundred battles, you will never be defeated.
When you are ignorant of the enemy but know yourself,
If ignorant both of your enemy and of yourself,
|
All TSCM Inspections should include (at least) the following frequencies with an examination of both radiated and conducted signal pathways. Expect to see less than ten milliWatt maximum on the antenna, and for the signal to be present for only a small amount of time.
Audio Detection 300 Hz to 15 kHz Base Band Audio Ultrasonic 10 kHz to 150 kHz Ultrasonic AudioVLF-Free Space 20 kHz to 350 kHz Video Cameras & Tape recorders
Carrier Current .3 kHz to 50 MHz 99% Voice (CC and PLA) Carrier Current 10 MHz to 450 MHz 99% Voice (AC Mains Antenna)
Free Space-HF 3 kHz to 50 MHz 99% Voice Free Space-VHF 30 MHz to 300 MHz 10% Video/80% Voice/10% Data Free Space-UHF 300 MHz to 900 MHz 25% Video/60% Voice/15% Data
Free Space-MW1 900 MHz to 3.0 GHz 50% Video/40% Voice/10% Data Free Space-MW2 3 GHz to 18.0 GHz Mostly Video and Data Free Space-MW3 18 GHz to 26.5 GHz Mostly Video and Data Free Space-MW4 26.5 GHz to 40.0 GHz (optional, based on threat)
...and of Course UV/Infrared! (Look for "Blooms")
150 - 450 nm Modulated UV Light Bugs 350 - 700 nm Modulated Visible Light Bugs (450 to 675nm very common) 700 - 1100 nm Audio Transmitters/Lasers (880 to 950nm very common) 800 - 1510 nm Audio Transmitters/Laser Microphones (rare)
750 - 900 nm Night Vision Illuminators 850 - 1750 nm IR Bugs and IR Illuminators
...and optical bugs installed INSIDE light bulbs and fixtures
450 nm - Modulated Tungsten bugs 490 nm - Modulated Sodium bugs 575 nm - Modulated Fluorescent bugs


An eavesdropping device may use the AC power circuits, telephone wiring, cable TV, or HVAC system wiring, as the transmission path (300 Hz to 450 MHz+), and may also use digital modulation or spread spectrum technology.
To find RF transmitters a search grid of less then 10 by 10 foot is used, and everything that causes any kind of deviation in the noise floor is investigated. Every cubic centimeter of the facility must also be carefully inspected with visual and electronic techniques.
For frequencies above 1 GHz a amplified dual ridged wave guide or standard gain horn (15-18 dBi) and low noise amplifier can be used to collect the signals (.5 GHz - 3 GHz, 1 GHz - 18 GHz, 18 - 26.5 GHz, 26.5 - 40 GHz, etc). The goal is to use highly directional horns, and then to amplify the signal to a high enough level to overcome all instrument noise and cable/connector losses.
Look for any electromagnetic energy on the RF spectrum, and not just specific modulation types. Once the source of the electromagnetic anomaly is identified then the modulation can be carefully analyzed to identify the signal type.
Remember: Bugs are always installed in groups of at least three: the one that was easy to find (the fools bug), the one that you will find if you really work hard (the novices bug), and then the real bug; that's almost impossible to find (the professional spies bug).
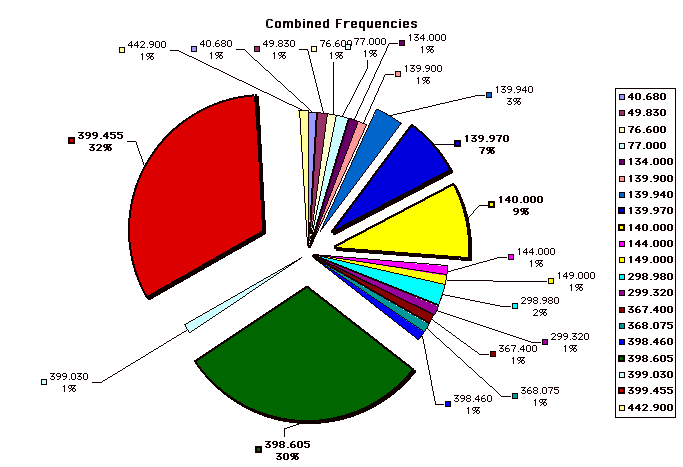
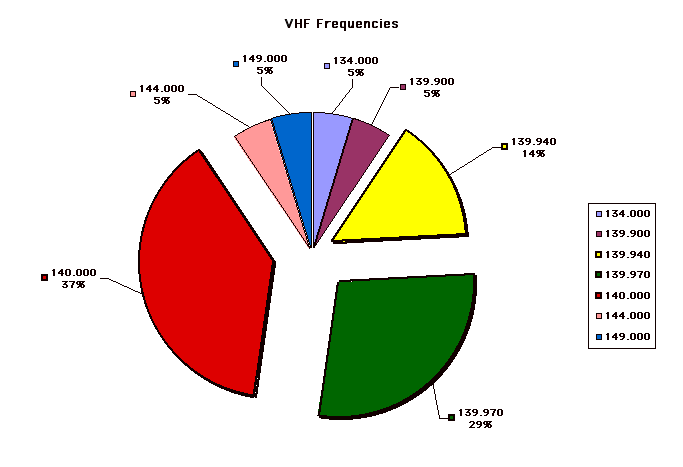
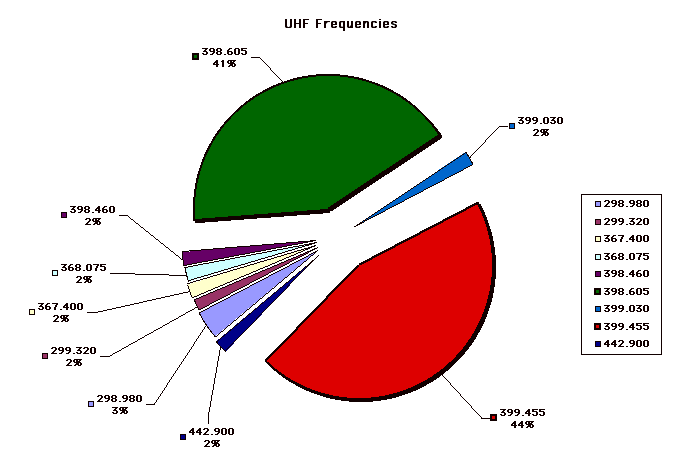
A microphone or video camera used for surveillance may be hundreds of feet away from the transmitter or recorder so be sure to check all potential transmission paths and not just the power and phone lines.
In a thorough TSCM inspection; RF Spectrum Analysis and monitoring should take place for at least twelve solid hours before a regular sweep. This part of the inspection is performed the day before the actual sweep, and will involve monitoring the ambient electromagnetic spectrum at locations AWAY from the actual facility (distances range from several hundred yards to several miles away from the facility). In cases when it is not possible to examine the RF spectrum in advance of the sweep at least six hours of time during the actual sweep should be spent examining RF signals.
When properly performed, a careful inspection of the RF spectrum can detect eavesdropping devices even from a considerable distance. Due to this it is highly beneficial for the TSCM team to examine the RF spectrum near the place to be inspected, but not actually inside the suspect area. For example, it is very desirable for the TSCM specialist to set up their instruments a few hundred feet away from the area to be inspected, and to spend at least six hours performing an instrumented analysis. In some cases this can be a conference room elsewhere in the building, a store room, warehouse, or even from a non-de script van located out in the parking lot. A side benefit to this type of an analysis is that it is not intrusive or disruptive at all.
To prepare for IPM or "In-Place Monitoring" the spectrum should be passively evaluated and monitored (inside the facility) for at least two or three hour prior to the meeting, general six hours is best (plus at least an hour or two for even the most basic of external physical examinations).
Many bugs targeted against corporate entities will generally have a transmit frequency between 20 MHz and 3 GHz. For someone willing to spend a little more money; bugging devices can be easily obtained which operate in the 3 GHz to 21 GHz range and above. This means the person performing a TSCM inspection must always inspect well above and below these frequencies.
A good rule of thumb is to check to at least five times the fundamental frequency of any credible RF threat. Up to the tenth or fifteenth multiple is ideal, and is actual dictated by various government standards. The radio frequency and signal analysis portion of any TSCM inspection should cover at least 9 kHz to 21 GHz (30 Hz to above 110 GHz is ideal).
![]() Common Eavesdropping Frequencies used by Amateur
Eavesdroppers
Common Eavesdropping Frequencies used by Amateur
Eavesdroppers
![]() Professional and Law Enforcement Bugging Frequencies
Professional and Law Enforcement Bugging Frequencies
![]() Surveillance Device "House" Frequencies/Bands
Surveillance Device "House" Frequencies/Bands
![]() Federal Surveillance Frequencies
Federal Surveillance Frequencies
![]() Surveillance and Spy Satellite Frequencies
Surveillance and Spy Satellite Frequencies
![]() Spread Spectrum and Frequency Hopping
Bug Frequencies
Spread Spectrum and Frequency Hopping
Bug Frequencies
![]() Bandwidth Resolutions and Filters
Bandwidth Resolutions and Filters

|
Therefore, I say: Know your oppositions capabilities and know your own equipment; in a thousand bug sweeps, you will never miss a bug.
When you are ignorant of your oppositions capabilities but know your own equipment,
If ignorant both of oppositions capabilities and of your own equipment,
|
50 - 750 kHz - Carrier Current Bugs (power, phone, HVAC lines) 25 - 80 MHz Ultra low power devices (micro watt devices) 65 - 130 MHz Micro power Part 15 devices (FM broadcast band) 130 - 150 MHz Body Wires and Wireless Microphones - Band I 150 - 174 MHz Body Wires and Wireless Microphones - Band II 174 - 225 MHz Body Wires and Wireless Microphones - Band III295 - 310 MHz Spread Spectrum and Micro powered Bugs (micro watt devices)
330 - 440 MHz Audio/Video Bugs (398.605, 300.455, and 399.030 MHz are popular) 430 - 550 MHz Audio/Video Bugs (433.920 and 418 MHz is popular) 800 - 990 MHz Audio/Video Bugs (902-985 MHz ISM band is popular)
1.10 - 1.95 GHz Video and Audio (980 MHz to 1.45 GHz is very popular) 2.00 - 2.75 GHz Video and Audio (2.4 to 2.45 GHz is extremely popular) 5.60 - 7.50 GHz Video and Audio (5.8 to 6.2 GHz is becoming very popular) 8.10 - 13.00 GHz Video and Audio (Popular)
850 - 950 nm Infrared Transmitters
DC - 3 kHz Typical Audio Band
3 kHz - 500 kHz Skin Effect (Non Radiating)
500 kHz - 3 MHz Non Radiating, Conducted RF
3 MHz - 300 MHz Conducted RF, Free Space Radiating
300 MHz - 3 GHz Free Space Radiating RF, Slightly Directional
3 GHz - 22 GHz Free Space, Low Attenuation., Highly Directional
22 GHz - 60 GHz Water Vapor Absorption Band
60 GHz - 3 Thz Limited Usage For Covert Surveillance

WARNING:
The area
between 3 GHz and 40 GHz is a serious threat as the
eavesdropping equipment in that range is inexpensive, readily
available, very low power, and highly directional. Additionally,
many TSCM people tend not to check frequencies above 1 GHz or 3
GHz (because the equipment is an order of magnitude too
expensive for them to buy). Beware of any TSCM specialist who
tries to convince you that there are no eavesdropping devices
above 3 GHz (it is usually a dead give-away that they don't own
any real counter-measure gear).
|
To be contacted for a confidential consultation please E-mail: jmatk@tscm.com
or send a letter via US Mail to:
or call:
URL: http://www.tscm.com/ |